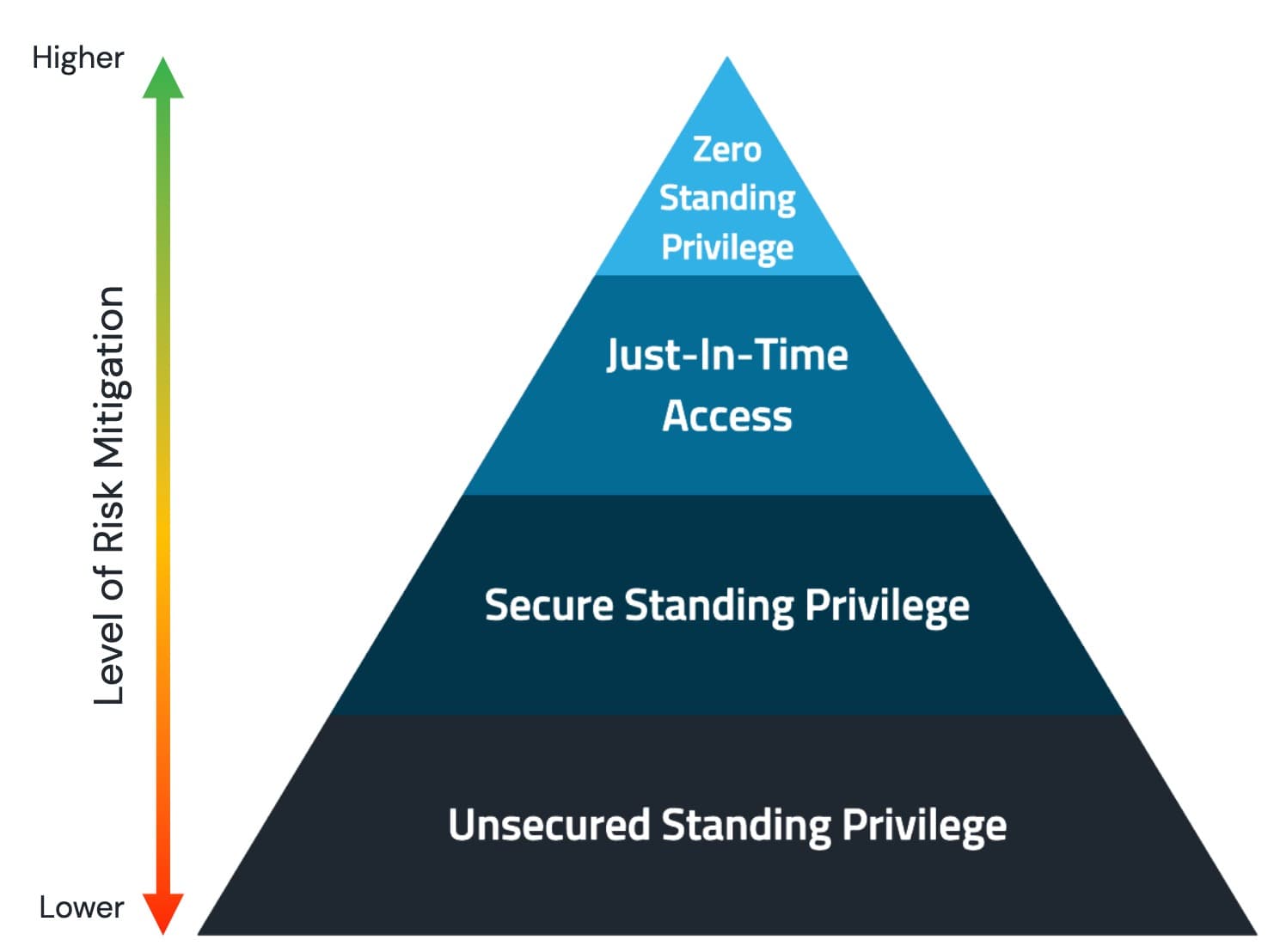
The Problem
- Privileged credentials (admin accounts, root access, service accounts) shared via spreadsheets or sticky notes
- No visibility into who accessed critical systems, when, and what actions they performed
- Former employees and contractors retaining access to privileged accounts long after departure
- Compliance failures in SOC 2, PCI DSS, HIPAA, and other frameworks requiring privileged access controls
- Insider threats and compromised credentials leading to data breaches and system compromise
Our Solution
Privileged Credential Vaulting
Centralized, encrypted storage for all privileged passwords, SSH keys, and API credentials
Just-in-Time Access
Time-bound, temporary privileged access with automatic revocation and approval workflows
Session Recording & Monitoring
Complete recording and real-time monitoring of privileged sessions for audit and security
Automated Password Rotation
Scheduled rotation of privileged credentials with zero-downtime for applications
Access Request Workflows
Approval chains and ticketing integration for privileged access requests
Comprehensive Audit Logging
Detailed logs of all privileged activities for compliance and forensic analysis
What's Included
Discovery & Risk Assessment
Week 1-2- Privileged account inventory across all systems
- Current access control audit
- Compliance gap analysis (SOC 2, PCI DSS, HIPAA)
- Risk assessment and threat modeling
- PAM architecture design and tool selection
Platform Implementation
Week 3-8- PAM solution deployment (CyberArk, BeyondTrust, or similar)
- Privileged credential onboarding and migration
- Integration with Active Directory, LDAP, SSO
- Access policy configuration and role definitions
- Session recording and monitoring setup
- Approval workflow implementation
Automation & Integration
Week 9-12- Automated credential rotation for databases and systems
- Application integration for credential retrieval
- SSH key management and rotation
- Service account password management
- Emergency break-glass procedures
- SIEM and SOC integration for alerting
Training & Compliance
Week 13-14- Administrator training on PAM operations
- End-user training for privileged access requests
- Security team training on monitoring and incident response
- Compliance documentation and evidence collection
- Runbooks and standard operating procedures
- 30-day post-launch support
Return on Investment
90% Reduction
In privileged credential exposure and security incidents
100% Visibility
Into all privileged access activities and sessions
Compliance Ready
Meet SOC 2, PCI DSS, HIPAA privileged access requirements
Investment
Starter
$25,000
Small team, basic PAM setup
- Up to 50 privileged accounts
- Core credential vaulting
- Basic access workflows
- Password rotation automation
- Standard reporting
- 8-10 week timeline
Most Popular
Professional
$45,000
Enterprise PAM with full features
- Up to 250 privileged accounts
- Session recording and monitoring
- Just-in-time access provisioning
- Advanced approval workflows
- SIEM integration
- Application credential management
- Compliance reporting
- 10-14 week timeline
Enterprise
$60,000+
Large-scale, multi-region PAM
- Unlimited privileged accounts
- Multi-region deployment
- Advanced threat analytics
- Custom integrations
- Privileged session analytics
- Risk scoring and alerts
- 24/7 monitoring support
- Dedicated security advisor
- 12-16 week timeline
Ready to Secure Privileged Access?
Schedule a free 30-minute consultation to discuss your PAM needs