Zero Trust Architecture: Why Perimeter Security Is Dead
Dennis Weston
November 27, 2025
Quick Navigation
- The Problem
- What Zero Trust Actually Means
- The Zero Trust Model
- Implementation Strategy
- Common Mistakes
- Your Next Move
The Problem
Your network perimeter doesn't exist anymore.
Employees work from home, coffee shops, airports. Applications run in AWS, Azure, GCP. Data lives in SaaS platforms. Partners access your systems directly. The "inside" and "outside" of your network have blurred to the point of meaninglessness.
Yet many enterprises still operate on a castle-and-moat security model: hard exterior, soft interior. Once someone is "inside" the network—whether through VPN, compromised credentials, or physical access—they can move laterally to access systems they shouldn't touch.
Why This Fails
A single compromised credential grants access to everything "inside" the perimeter. We've seen attackers use one phished employee password to access databases containing millions of customer records, financial systems, and intellectual property.
The 2013 Target breach started with stolen HVAC vendor credentials. Those credentials shouldn't have provided access to payment systems, but the flat network architecture allowed lateral movement from HVAC systems to point-of-sale terminals. 40 million credit cards were compromised.
Perimeter security assumes trust based on location. Zero Trust assumes breach and verifies everything.
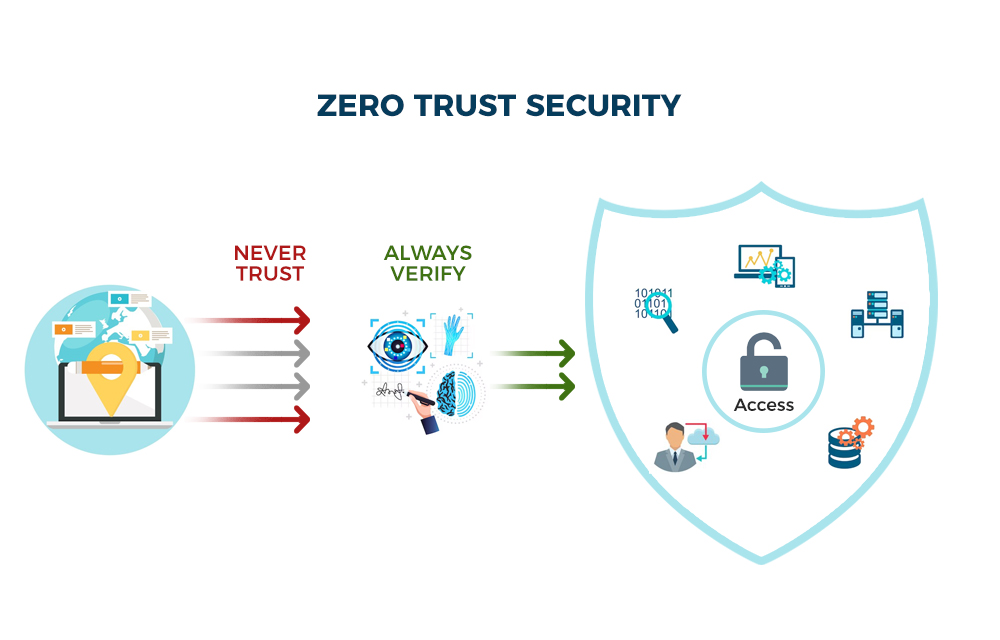
What Zero Trust Actually Means
Zero Trust is not a product. It's an architecture based on a simple principle: never trust, always verify.
Every access request—regardless of where it originates—must be authenticated, authorized, and encrypted. Trust is never implicit. Location doesn't grant privilege. Being "on the corporate network" means nothing.
Core Principles
Verify explicitly. Always authenticate and authorize based on all available data points—user identity, device health, location, application sensitivity, data classification, and anomaly detection. Never assume trust.
Use least privilege access. Grant users the minimum access required to complete their task. Just-in-time and just-enough-access. Limit blast radius if credentials are compromised.
Assume breach. Operate as if attackers are already inside your network. Segment access. Encrypt everything. Monitor all activity. Minimize lateral movement.
The Zero Trust Model
Zero Trust architecture requires several components working together:
Identity-Based Access Control
Identity becomes the new perimeter. Users and devices prove who they are before accessing any resource.
This means strong authentication (multi-factor), continuous verification (not just at login), and context-aware policies (user role, device posture, location, time, data sensitivity).
Micro-Segmentation
Break the network into small zones. Each zone requires separate authentication. An attacker who compromises one system can't automatically pivot to others.
Traditional VLANs segment at Layer 2/3. Micro-segmentation works at Layer 7, understanding applications and data flows. Access policies follow workloads regardless of where they run—on-premise, cloud, or hybrid.
Continuous Verification
Authentication isn't a one-time gate. It's continuous throughout the session.
Monitor behavior. Detect anomalies. If a user suddenly accesses resources they've never touched, from a location they've never visited, trigger additional verification or block access entirely.
Data-Centric Security
Protect data wherever it lives. Encrypt at rest and in transit. Apply access policies based on data classification. Track who accesses what data and when.
Even if an attacker gains network access, they can't read encrypted data without proper authorization.
Implementation Strategy
Phase 1: Map Your Environment
You can't protect what you don't understand. Catalog all assets, data flows, and access patterns.
Identify your crown jewels. What data, applications, and systems would cause the most damage if compromised? Start Zero Trust controls there.
Document current access. Who accesses what? How? From where? This baseline reveals over-privileged accounts and unnecessary lateral movement paths.
Classify data. Not all data requires the same protection. Classify by sensitivity and apply appropriate controls.
Phase 2: Implement Strong Identity
Identity is the foundation. Without reliable authentication, Zero Trust fails.
Deploy multi-factor authentication (MFA) everywhere. Not just for remote access. For all systems, all users, all the time. Modern MFA uses hardware tokens, biometrics, or push notifications—not SMS codes that can be intercepted.
Implement single sign-on (SSO). Centralize authentication. Apply consistent policies across all applications. Reduce credential sprawl.
Enable conditional access. Allow or deny access based on context: device compliance, location, risk level, application sensitivity.
Phase 3: Segment Networks and Applications
Break the flat network into isolated segments.
Micro-segmentation - Define policies at the application level. Database servers only accept connections from specific application servers. Those application servers only accept requests from authorized users.
Software-defined perimeters - Create dynamic, identity-based perimeters around resources. Users connect directly to applications, not to the broader network.
Service mesh for containers - Enforce mutual TLS between microservices. Every service-to-service communication is authenticated and encrypted.
Phase 4: Monitor and Respond
Zero Trust generates massive amounts of security telemetry. Use it.
Log everything. Authentication attempts, access grants, data flows, configuration changes. Centralize logs for analysis.
Detect anomalies. Baseline normal behavior. Alert on deviations. A user accessing a file server at 3am from a foreign country deserves investigation.
Automate response. When high-risk activity is detected, automatically trigger additional authentication, restrict access, or isolate the user/device.
Common Mistakes
Treating Zero Trust as a Product
Vendors sell "Zero Trust solutions." These are tools that support Zero Trust architecture, not Zero Trust itself.
You can't buy Zero Trust. You build it through strategy, process, and the right combination of tools—identity management, network segmentation, encryption, monitoring, and policy enforcement.
Trying to Do Everything at Once
Zero Trust is a journey. Trying to implement it enterprise-wide on day one guarantees failure.
Start with high-value assets. Prove value. Learn lessons. Then expand incrementally.
Ignoring User Experience
Poorly implemented Zero Trust frustrates users. Excessive authentication prompts. Denied access to legitimate resources. Slow performance.
Users will find workarounds—personal devices, shadow IT, shared credentials—that bypass your controls entirely.
Balance security with usability. Use risk-based authentication: low-risk activities require minimal friction, high-risk activities require stronger verification.
No Clear Metrics
How do you measure Zero Trust progress? Common metrics include:
- Percentage of applications behind identity-based access controls
- Percentage of network traffic micro-segmented
- Mean time to detect lateral movement
- Number of privileged accounts with just-in-time access
- Percentage of authentication events using MFA
Track metrics. Show progress. Justify investment.
Your Next Move
Audit your current state. How much implicit trust exists in your environment? Where are the gaps?
Identify quick wins:
- Enable MFA on critical systems
- Segment access to sensitive databases
- Implement just-in-time privileged access
- Deploy device health checks before granting access
Each improves security immediately while building toward comprehensive Zero Trust architecture.
Work With Us
Tech Blend specializes in Zero Trust architecture for enterprises. We've helped organizations transition from perimeter-based security to identity-centric models that actually protect against modern threats.
If your organization needs help with:
- Zero Trust strategy and roadmap
- Identity and access management implementation
- Micro-segmentation and network security
- Compliance in Zero Trust environments
Get in touch: Email us at sales@techblendconsult.io
References
Want more insights like this?
Subscribe to get weekly DevSecOps guides, security best practices, and infrastructure tips delivered to your inbox.
No spam. Unsubscribe anytime.